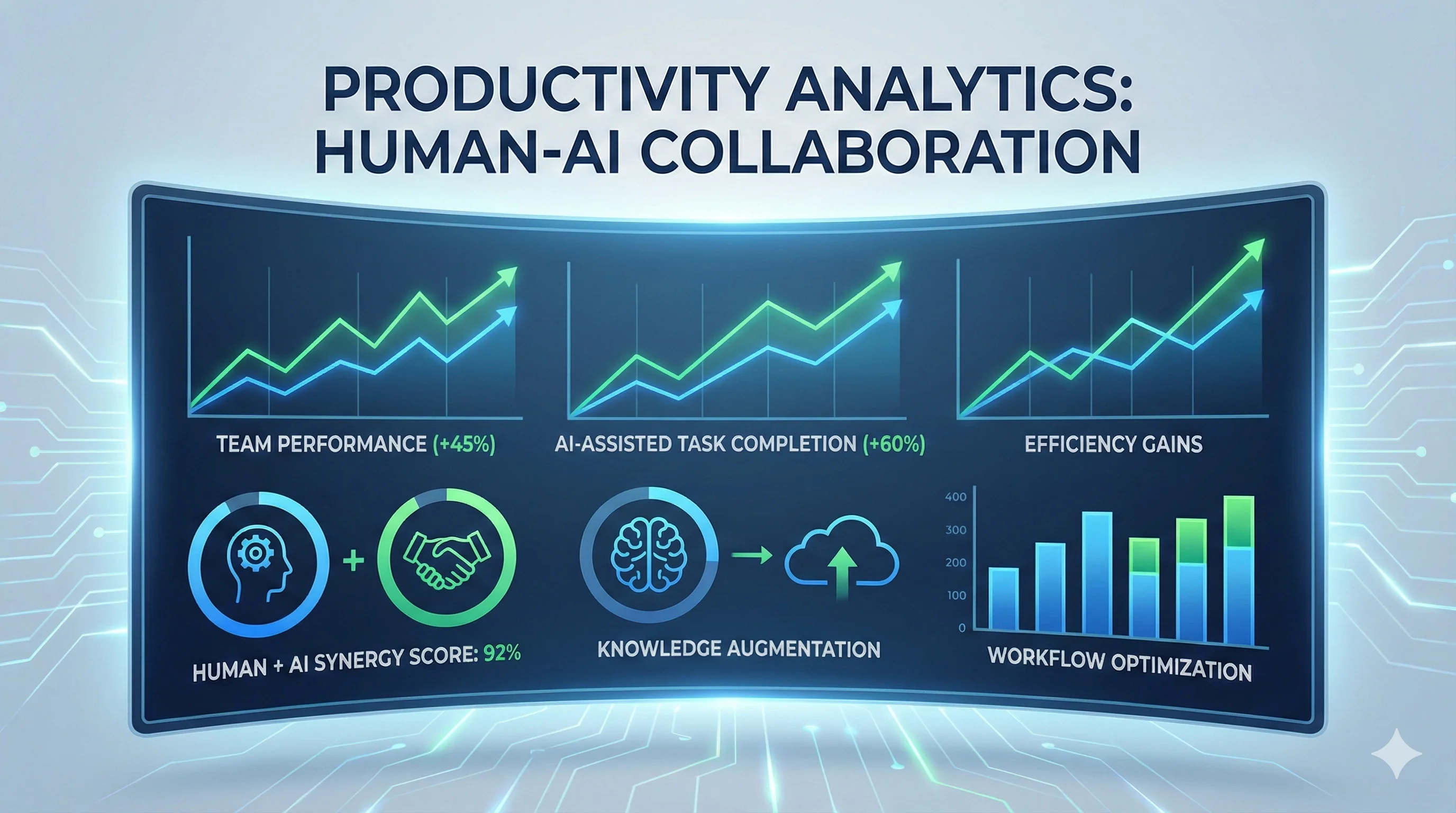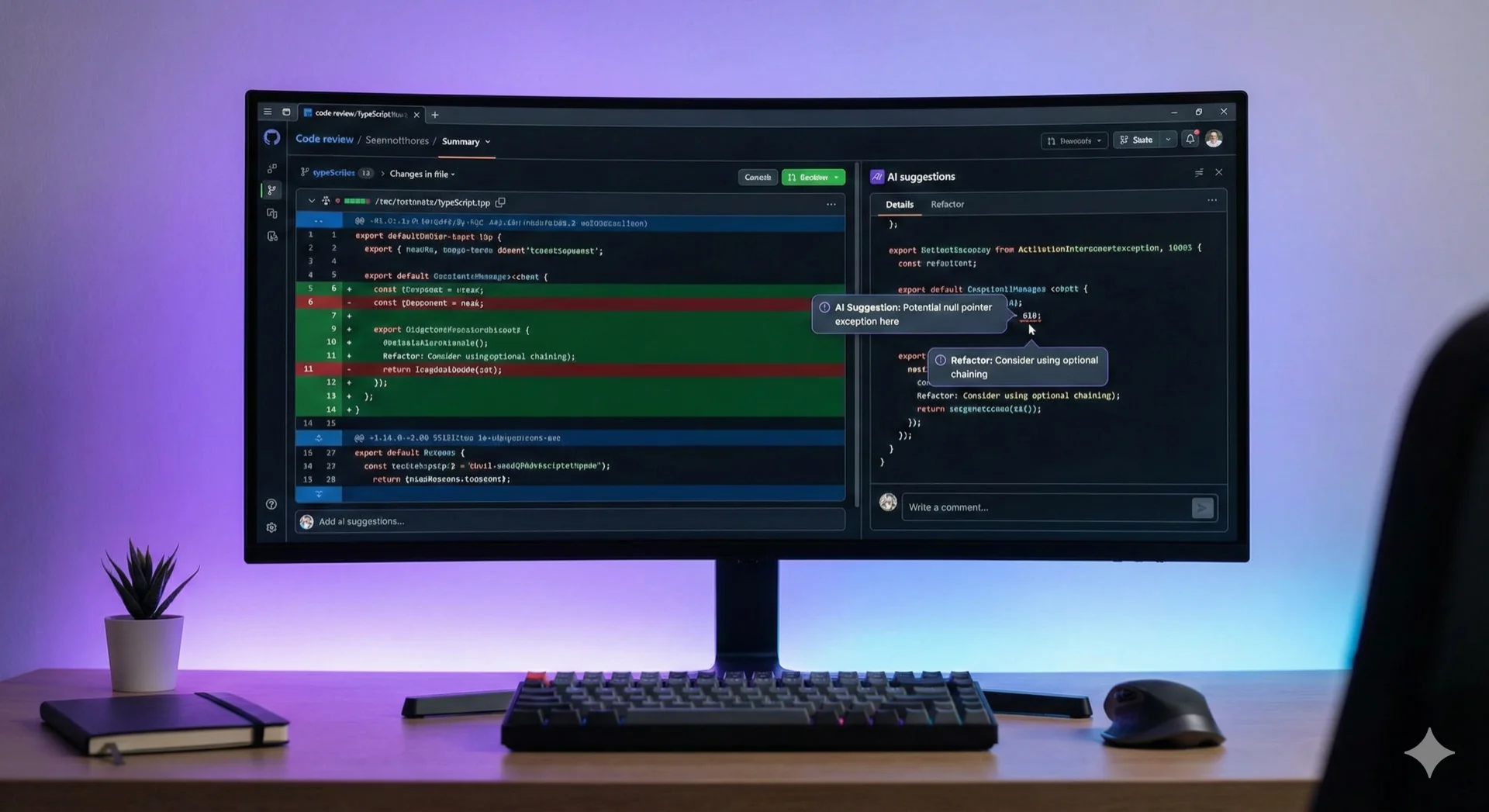
AI-Assisted Code Review: A Practical Framework
This is Part 4 of “The Centaur’s Toolkit” series, where we explore practical strategies for human-AI collaboration in technical work. Code review is one of those practices everyone agrees is important and almost nobody enjoys. You’re deep in your own work when a PR notification arrives. You context-switch, try to understand someone else’s mental model, and attempt to provide useful feedback before the next interruption hits. It’s mentally draining. And honestly, most reviews end up being superficial because thorough review takes time nobody has. ...